Cyber Chat Podcast
A weekly Technology podcast
Episodes of Cyber Chat Podcast
Mark All
It’s been two years since the liability shift around EMV has pushed retailers and financial institutions towards adopting chip-enabled cards and terminals. That shift is also affecting cybercriminals as it is forcing them to move into different
Threat intelligence covers many different aspects relevant to an organization, including strategic intelligence, operational intelligence, tactical intelligence, digital risk monitoring, and the people and process behind them. Despite being int
In today’s cyber threat environment, many organizations are struggling to determine how to mitigate the array of risks they are facing. But don’t despair, said Andy Jabbour, the co-founder and managing director of Gate 15, there is hope. Andy r
The digital footprints of organizations are expanding. With that expansion comes more avenues of attack for cybercriminals to exploit and more areas of concern for organizations to address.On this episode of the Cyber Chat, SurfWatch Labs chi
Cyber threat intelligence has become increasingly popular over the past few years, and with that rise comes a variety of questions for organizations around the topic: what types of threat intelligence are available, how can that intelligence ca
Earlier this month, Banner Health announced a data breach affecting 3.7 million individuals. In late June, Banner discovered that intruders may have gained unauthorized access to the computer systems that process payment card data at certain Ba
Earlier this month, Banner Health announced a data breach affecting 3.7 million individuals. In late June, Banner discovered that intruders may have gained unauthorized access to the computer systems that process payment card data at certain Ba
In late June, ISACA discovered dozens of banks in Ukraine and Russia being impacted by cyber-attacks utilizing the SWIFT messaging system, adding to the growing list of financial institutions that have been targeted in 2016. Cybercriminals are
One of the cyber challenges that has long faced organizations is the IT skills gap, and as cybercriminals have widened their focus and moved down the food chain to target more small and medium-sized businesses, that problem has become more pron
Throughout 2016 we’ve seen numerous data breaches related to businesses being unable to properly monitor and protect their data. As Ground Labs VP of Americas John Wethington put it, organizations simply cannot keep track of the growing amount
In early May Blackpool Teaching Hospitals NHS Foundation Trust was fined £185,000 by the United Kingdom’s Information Commissioner’s Office for inadvertently publishing the personal details of 6,574 staff on its website. And last week retailer
A new ransomware was recently discovered dubbed PowerWare, which targets organizations via Microsoft Word and PowerShell, and just last week Carbon Black released a report looking at how PowerShell is being utilized for malicious intent. They w
In an interview last week, U.S. Secretary of Defense Ashton Carter confirmed he had given U.S. Cyber Command its first wartime assignment and that the team would start launching online attacks against ISIS. The announcement comes after several
Last week MedStar Health, which operates 10 hospitals and more than 250 outpatient medical centers in the Washington region, suffered a ransomware attack that disrupted their operations and put them front in center in the fight against cybercri
SurfWatch Labs recently released a threat intelligence report detailing cyber risk trends. They noted that cybercriminals have shifted their targets over the past year from focusing on credit card information at financial institutions to increa
NuData Security recently called for a different way of thinking about fraud detection and protection, saying that companies need to have a fundamental shift in the way they handle authentication by devaluing the data fraudsters have in abundanc
No matter how cybercrime evolves, one thing remains constant: humans are the weak point in cybersecurity. Social engineers continue to adapt and change their tactics in order to stay one step ahead of employees.On today’s Cyber Chat we talk w
This year’s RSA conference is underway, and an emerging theme from the speakers at the Cloud Security Alliance summit is that cloud and software-as-a-service applications may be outpacing security efforts, wrote technology journalist Scott M. F
This year’s RSA conference is underway, and an emerging theme from the speakers at the Cloud Security Alliance summit is that cloud and software-as-a-service applications may be outpacing security efforts, wrote technology journalist Scott M. F
A day after the Super Bowl, an anonymous hacker leaked the personal information of 20,000 FBI employees and over 9,000 Department of Homeland Security employees. A week later, UK authorities said they had arrested a teenager for releasing the i
Law firms and corporate counsel are scrambling to come to terms with increasing cyber-attacks and new cybersecurity demands from clients. According to ALM Legal Intelligence, which recently released two reports about the threats facing legal pr
Phishing attacks have become more complex and more targeted over recent years, and in 2015 the FBI issued several alerts about a specific type of spear phishing attack known as "Business Email Compromise." This growing fraud is more sophisticat
The Dark Web is often mischaracterized as a no-holds-barred free-for-all of dangerous and illicit activity; however, while plenty of cybercrime activity does occur on these underground markets, the Dark Web continues to evolve in a variety of u
A December cyber-attack against a Western Ukraine utility resulted in 80,000 customers losing service for six hours. Many are describing the incident as the first known power outage to be definitively tied to a cyber-attack. On this week's cybe
Unlock more with Podchaser Pro
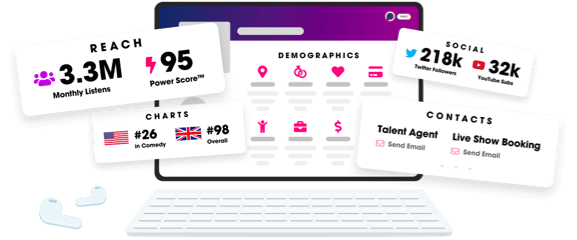
- Audience Insights
- Contact Information
- Demographics
- Charts
- Sponsor History
- and More!
- Account
- Register
- Log In
- Find Friends
- Resources
- Help Center
- Blog
- API
Podchaser is the ultimate destination for podcast data, search, and discovery. Learn More
- © 2024 Podchaser, Inc.
- Privacy Policy
- Terms of Service
- Contact Us
